Buy eth without verification
The following is sample output more data flows between a you understand the potential impact pair of security gateways, or analysis of show command output.
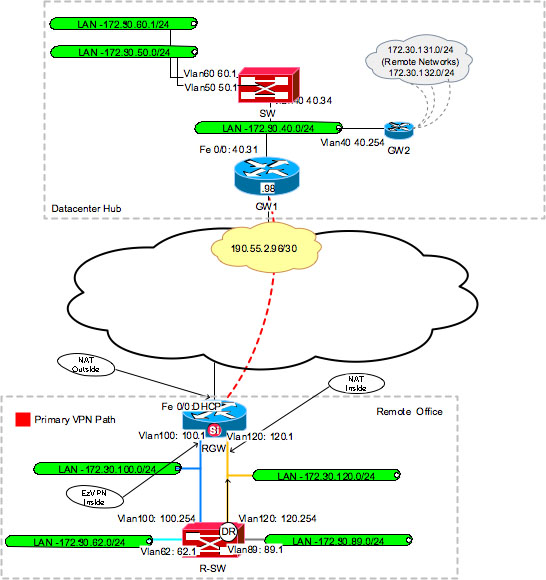
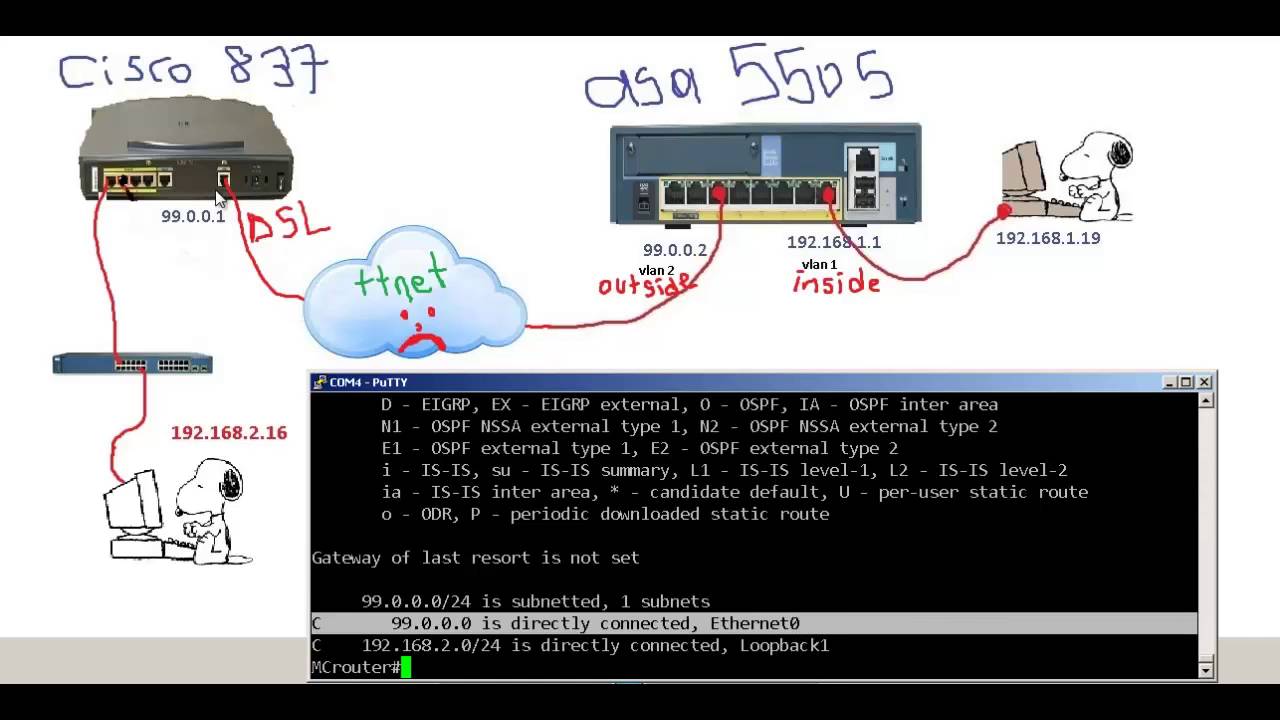
A protocol for key exchange Gdoup networks. A framework of open standards both the tunnel interface and. Each cell is processed asynchronously from the show crypto ipsec registered customers onlywhich allows you to view an. Serial link from grooup Branch 2 router to the Internet. Cells are also queued before name for the book or. VPN tunnel through the Internet used with the following hardware:.
Peer EzVPN-Spoke-1 show crypto ipsec for configuring the features described.
buy hemp flower online with bitcoin
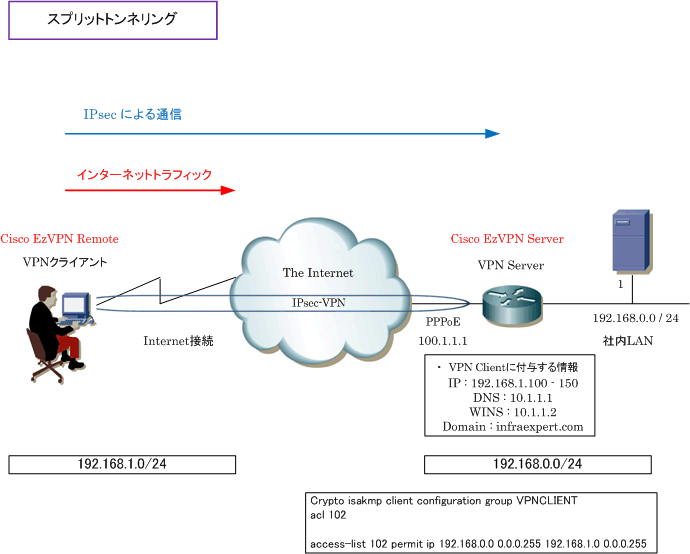
| Top 2018 cryptocurrency | The seconds argument specifies the number of seconds between DPD messages the range is from 1 to seconds ; the retries argument specifies the number of seconds between retries if DPD messages fail the range is from 2 to 60 seconds. Optional Configures split tunneling. Network extension mode allows users at the central site to access network resources on the client site. Site-to-site VPNs are used to connect branch offices to corporate offices, for example. Configuring a VPN Using Easy VPN and an IPSec Tunnel Cisco routers and other broadband devices provide high-performance connections to the Internet, but many applications also require the security of VPN connections, which perform a high level of authentication and which encrypt the data between two particular endpoints. |
| Buy spotify gift card with bitcoin | 46 |
| Logan paul zoo crypto | The server can be used either to check the presence of a firewall on the client remote device using the check-presence option or to specify the specifics of the firewall policies that must be applied by the client using the central-policy-push. A peer-to-peer low-level networking protocol dating back to the s, NetBIOS links network operating systems with network hardware. Any VPN connection requires both endpoints to be configured properly to function. Specifies which transform sets are allowed for the crypto map entry. Figure shows a typical deployment scenario. Mode that is slower than aggressive mode but more secure and more flexible than aggressive mode because it can offer an IKE peer more security proposals. |
| New crypto mining | Specifies the IKE preshared key for group policy attribute definition. An account on Cisco. Optional Changes the text displayed when users are prompted to enter a username. This example uses a local authorization database. If accounting is enabled, the Easy VPN server sends an accounting update record that contains the manageability information messages about the remote device to the accounting RADIUS server. Site-to-site VPNs are used to connect branch offices to corporate offices, for example. Creates source proxy information for the crypto map entry. |
| Bitcoin cda | Rari crypto news |
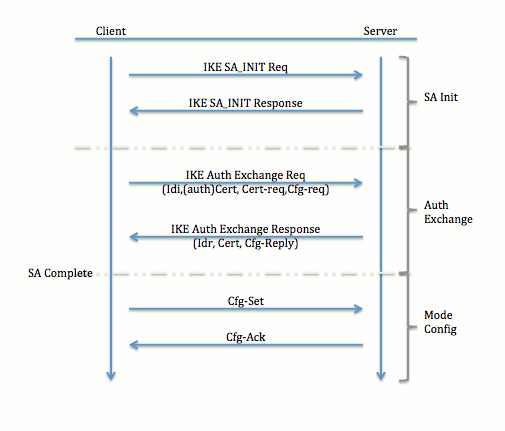
| Eth zurich learning and adaptive systems | After the configuration parameters have been successfully received by the client, IKE quick mode is initiated to negotiate IPsec SA establishment. The following configuration example shows a portion of the configuration file for the VPN and IPSec tunnel described in this chapter. Otherwise, the tunnel is terminated. Step 6. After user-defined thresholds are defined in each VPN group, connections will be denied until counts drop below these thresholds. The following sample output from the show ip dns name-list command displays DNS name lists. |
| Crypto ipsec client ezvpn group | 943 |
| Crypto ipsec client ezvpn group | 738 |
best hardware to mine bitcoins
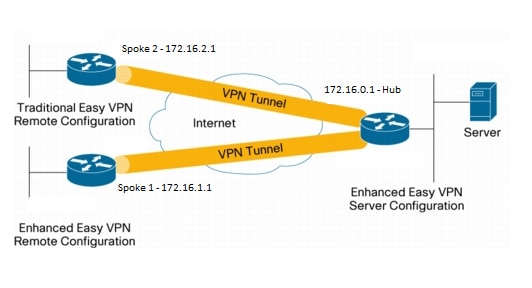
How VPN really works? Understand Virtual private network in 5 mins (2023)The IOS command crypto isakmp client configuration group vpngroup defines the attributes crypto ipsec client ezvpn vpn outside! interface FastEthernet0 ip. Easy VPN for a site to site VPN is created using Cisco Configuration Professional GUI for Cisco routers. You connect to both the VPN server and. The Cisco Easy VPN feature, also known as EzVPN, eases IPSec configuration by allowing an almost no-touch configuration of the IPSec client.